More Isn't Always Better: Targeting Tips for Quality Website Traffic
Why reaching fewer people can deliver stronger campaign results, gain quality website traffic, and bring in better bidders.
When it comes to paid advertising, it can be easy to get stuck in the mindset that bigger is always better. But, contrary to popular belief: it’s not. After launching a campaign, it’s hard to not get excited when thinking about the surge of new website visitors and traffic that the campaign is sure to bring in. However, it’s important to manage expectations and realize that while hundreds or even thousands of new website visitors may seem like a great thing at first, it’s not always what it seems.
Would you rather get 100 users on your website that don’t bid on anything, or 20 users who bid in your auctions with a few who even end up becoming winning bidders? That’s right – you’d choose the 20 over the 100. This is something to keep in mind when it comes to choosing audience targeting and website traffic results for digital marketing efforts.
Read on to learn why a smaller audience and less website traffic may be more ideal in the long run.
Audience Targeting
Before your auction marketing paid ad campaign is published out into the world, it’s important to consider your target audience and who you want to see your ads. It may be tempting to want to run your campaign with the widest reach possible and have your ads shown to as many people with as many different interests as possible, but that won’t get you the results you desire.
For example: when running a campaign for an antique auction, it wouldn’t be wise to target people who are looking to buy farm and construction equipment. Instead, it would be smarter to target people who like and want to buy antiques and collectibles. Even though the targeting options for antiques and collectibles may be smaller, the audience seeing the ads will be more receptive to them and have a higher chance of clicking on the ads, going to the website, and bidding in your auction!

Location Targeting
The same thing goes when it comes to choosing location targeting. If your antique auction is in Tennessee, and you don’t offer shipping, it’s a smart idea to keep the targeting more local to Tennessee, instead of targeting the whole United States. People in California are not going to be interested in buying items from a company in Tennessee that doesn’t offer shipping. While the number of people available to target in Tennessee is smaller, the audience seeing the ads would be more local and therefore more likely to bid on items and make the drive to pick them up if they win.
On the other hand, if you do offer national shipping and want to target a broader audience, that could work. Just make sure to refine your target audience based on interests as well to still have your ads seen by only the most relevant people.
If you are interested in slowly expanding your location targeting to be larger after running a few successful campaigns, always start local, test and monitor performance, then expand as budget and logistics allow. Remember, running a campaign over a larger geographic area also requires a larger ad spend budget, to adequately saturate the available audience. A $500 ad spend budget concentrated on one state will achieve stronger results and saturate the intended audience better than the same budget spread across multiple states.
Campaign Results
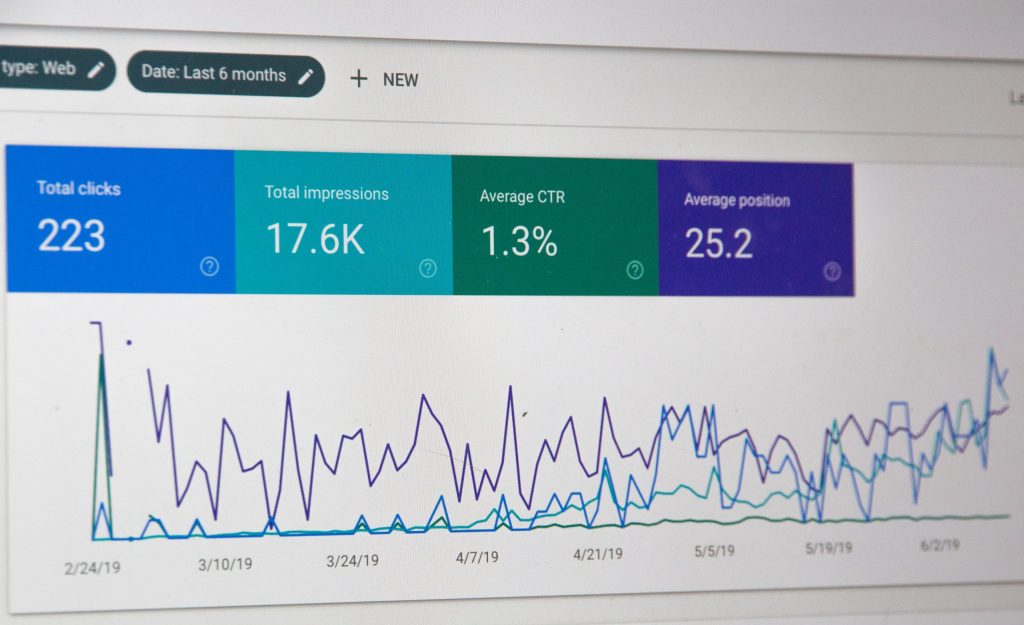
If you’re showing your ads to as many people as possible, with very loose targeting specifications, your campaign may receive a higher amount of reach and impression results, but those aren’t the best things to base the success of your campaign on. Just because more people see an ad, it doesn’t mean more of them are going to want to click on it. Getting an Impression means that someone simply saw your ad on their screen. If the ad isn’t relevant to them, they are going to keep scrolling past it and not take any further action to click to your site.
A better indication of increased website traffic is either link clicks or landing pages views. Both of those campaign stats will give a more accurate reflection of how your campaign is performing and how many users are really clicking your ad to get to your website and auctions. While seeing hundreds and thousands of impressions might feel good, it’s link clicks and landing page views that will really bring bidders to your site. While link clicks and landing page views are more costly than impressions, they hold more value and bring more quality traffic to your website.
Ultimately, it’s up to you to determine what audience and geographical area that you want to target for your ad campaigns and what website traffic is beneficial to you. It’s okay to start slow and not have the biggest audience or amount of website traffic right away. The key is to focus on a target audience that is genuinely interested and likely to engage with the ads, as well as the kind of users you really want on your website and bidding in your auctions.
If you stay consistent in your campaigns and marketing efforts, both your audiences and website traffic will grow with quality users who keep coming back!
Need help getting started? Our marketing team is waiting and ready to help! Sign up today to start implementing effective auction marketing campaigns and bringing quality traffic and bidders to your auctions!